Information systems’ security flaws are systematically reviewed in a vulnerability assessment. Assigns severity levels to vulnerabilities, determines whether the system is vulnerable to them, and suggests mitigation or remediation strategies as needed.
The following are some examples of hazards that vulnerability assessments can help prevent:
- Malicious code injection attacks, such as SQL injection and cross-site scripting (XSS).
- A rise in privileges is caused by ineffective authentication procedures.
- Software that comes with unsecured defaults, including easily-guessable administrator passwords, is known as insecure defaults.
Click here to order vulnerability assessment service.
Vulnerability evaluations come in various forms. Among them are:
- Critical servers, which might be assaulted if not properly tested or not built from a tested machine image, are evaluated during host assessments.
- The evaluation of procedures and policies aimed at thwarting intrusions into wireless and networked systems is known as a network and wireless security audit.
- Database evaluation involves checking databases and large data systems for security flaws and improper settings, finding malicious databases or unprotected development or testing environments, and categorizing sensitive information within an organization’s system.
- Scanning an application’s source code or conducting automated front-end scans is one way to find security flaws in a website’s code.
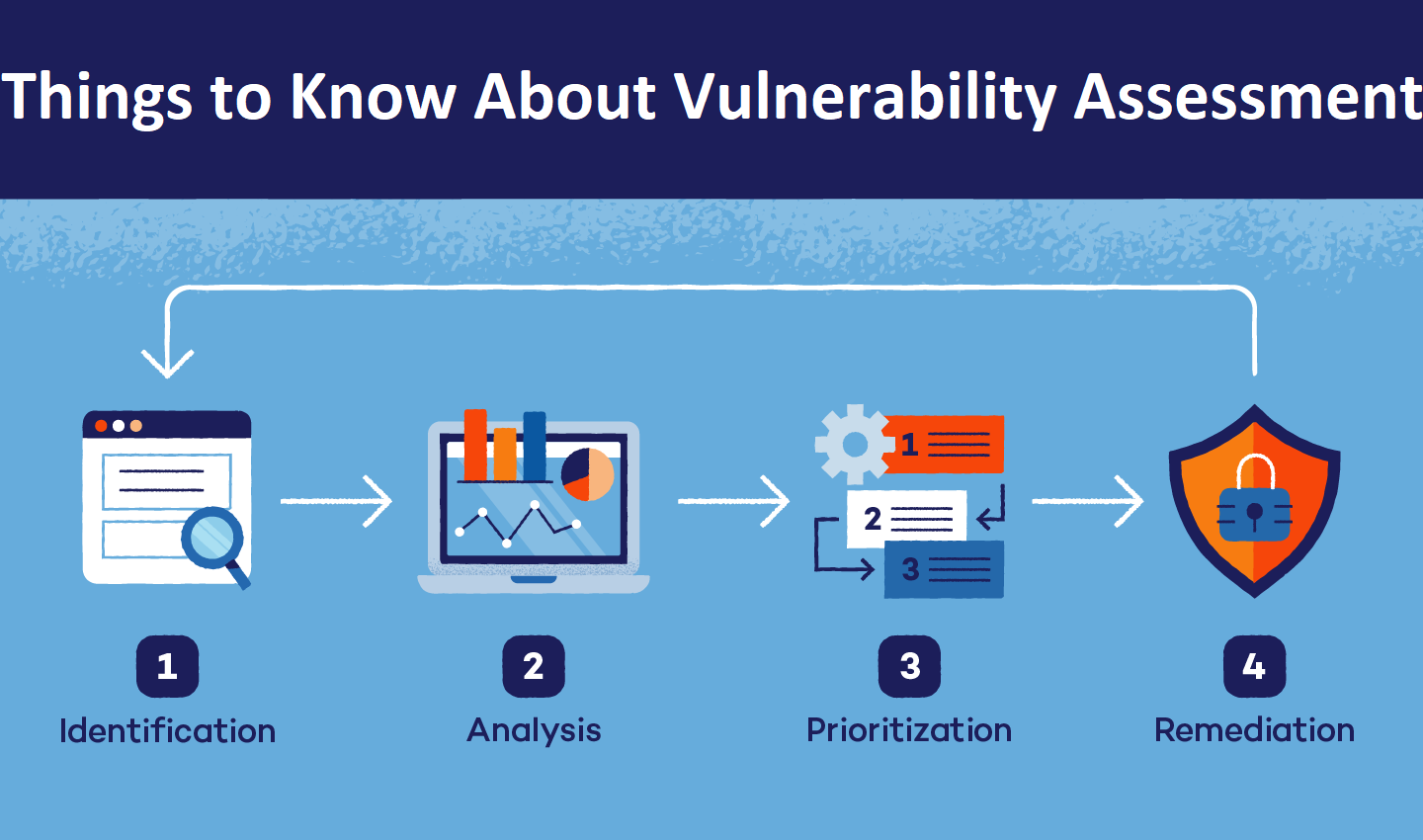
Security scanning procedure
Testing, analysis, assessment, and remediation are the four stages that make up the security scanning process.
1. Identifying vulnerabilities through testing
In this stage, you will compile a list of all the security holes in an application. Automated tool scans or manual testing and evaluation are two ways security analysts check the health of systems, applications, and servers. When looking for security holes, analysts also use threat intelligence feeds, asset management systems, vendor vulnerability notifications, and vulnerability databases.
2. Vulnerability assessment
Finding the origin and fundamental reason of the vulnerabilities mentioned in the previous step is the goal of this stage.
Finding the source of a vulnerability and the specific system component that is at fault is part of this process. Consider the possibility that an outdated open-source library version is at the heart of a security hole. There is now an obvious way to fix it: by enhancing the library.
3. Analyzing potential dangers
Vulnerability prioritization is the goal of this phase. The process begins with security experts considering several parameters and then ranking or scoring each vulnerability accordingly.
- Find out which systems are impacted.
- Tell me which data is in danger.
- Tell me which company operations are vulnerable.
- Compromise or attack ease.
- Attack intensity.
- Possible harm caused by the security hole.
4. Remediation
Sealing off security holes is the goal of this stage. When figuring out how to fix or mitigate a vulnerability, the development and operations teams, as well as the security professionals, usually work together.
Possible remedial actions could involve:
- The implementation of novel security protocols, policies, or instruments.
- The updating of operational or configuration changes.
- Fixing a security hole through code development and deployment.
It is not possible to do a vulnerability assessment just once. Organizations need to make this process operational and do it often if they want it to work. Additionally, DevSecOps—the practice of encouraging collaboration amongst development, operation, and security teams—must be prioritized.
Tools for Vulnerability Assessment
The purpose of vulnerability assessment tools is to detect and eliminate any security risks to your application automatically. Here are some examples of tools:
- Web application scanners that probe for and mimic common forms of attack.
- Software that scans a network for potentially exploitable protocols, ports, and services.
- Scanners for networks aid in visualizing networks and finding red flags such as rogue IP addresses, flooded packets, and unusual packet production originating from a single IP address.
It is recommended to set up automatic scans of all important IT systems regularly. The organization’s continuous vulnerability assessment process should be informed by the findings of these scans.